Introduction of Cryptography and Ciphers
Cryptography is to secure the message or information by encryption technique. It is used to store the message secretly and retrieve it by the end user. A Cipher is an algorithm used to encrypt or decrypt the message.
The cryptography word is divided into two parts. Crypto is derived from the Greek word Kryptos which means hidden and graphy is known as writing. It is termed as hidden writing. Cryptography is the science or study of techniques of secret writing or hidden writing.
Cryptography involves two major operations called Encryption and Decryption
Encryption is the process to convert the original text to cipher text by using a key. Original text is plain text and cipher text is encrypted text.
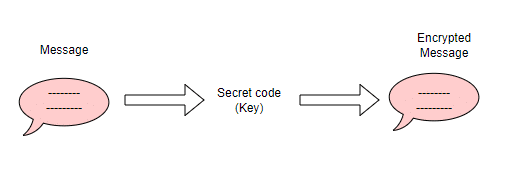
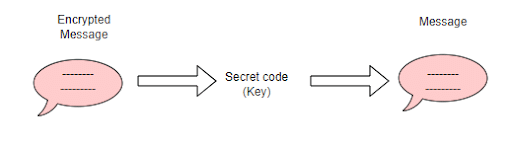
Decryption is the inverse process of encryption to convert back encrypted data into its original text. So both algorithms commonly use the key to the conversion process. Encryption and decryption algorithm called ciphers.
Cryptography ensures that no one can steal the message by sending back and through.
History of Cryptography
The history of cryptography started earlier than we could imagine. During historic periods, alias kingdoms used to share some message across miles which were usually carried by a person. They found that the message was getting leaked and the enemy kingdom got to know their battle strategies. This leads them to invent some idea to hide the details from the message using some riddle which again leads to misleading the alias kingdom which is supposed to understand the message.
One of the earlier uses of cryptography was found in Egypt at 1900 BC. In 486 BC Greece used scytales to send secret sensitive messages during times of battle. Both the sender and receiver have identical keys to read the messages. Caesar Cipher invented the simple encryption technique around 60/50 BC. Cipher text is shifting each letter down the alphabet and replaced by the letter some fixed number of positions. First they shifted by 3 numbers in the alphabets. It would take up to only 26 attempts to break the encryption of messages written in english. This method is easy to break by all possible shift values.
In 1797 Thomas Jefferson created the wheel which consists of 26 cylindrical wooden pieces of letters threaded onto an Oniron Spindle. The letters of the alphabet were inscribed on the edge of each wheel in random order. The recipient looks at the one line of messages that would make sense by scramble and unscramble words. This cipher can be brute forced by hand given sufficient time, and is of course no longer secure in the era of computers.
In 1918, Arthur scherdius invented one of the most famous cryptography machines in the world. When the key is pressed, one or more rotors rotate on the spindle. The secret key is connected with a unique electric hathway. For humans it is not possible to find the message, but computers make it easy.
In 1943, Alan Turing, one of the greatest mathematicians, designed an extremely sophisticated cipher machine which is used to reduce the work of code-Breakerson. Each time an encryption algorithm is compromised, a new one which is computationally more challenging to break is put forward.
In 1948, Claude E.Shannon was considered to be the father of modern cryptography. He was inspired by the problems of cryptography because secrecy systems furnish an interesting application of communication theory. He identified the three main goals of cryptography: secrecy, integrity and authenticity. Nowadays we have a solid theory that describes the cipher to be secure.
Hack 101
The history of cryptography teaches us why there were so many advancements of cryptography techniques being invented. Though there are many safer ways to encrypt and decrypt a message, the intruders (or commonly called hackers) use some way to crack the secret out of the hidden message. We should also think in hacker’s perspective inorder to get to know the disadvantages of our own cryptography algorithm. Lets also learn one of the simplest hacking strategies.
To encrypt and decrypt a message, normally we use some key either as numeric or alphanumeric code. The hacker will not be having the key but he will try some strategies such as brute force algorithms.
Check out the code provided below. The program uses a simplest known cipher algorithm called “Caesar Cipher”. In this program the message ‘HELLO’ is used with the key value is 5 that means each alphabet will be shifted to 5 characters. We first encrypt the message by using a key. The encrypted message is cipherText. Then decrypting the cipherText by using the same key value will provide us the plain text back. The hacker won’t be having the key but only the cipher text. The hacking part of the code, will iterate through all 26 possible keys over the cipher text. Each iteration validates the intermediate output across a known subset of common words (where in this program we only took very few known words for testing purposes). Whenever the intermediate output matches with any one of the known words, the program will break and inform that as the decrypted plain text. The program optionally prints null as failure of hacking where it couldn`t match with any of the known words. In that case, we may need to increase the number of known words.
Code
public class Hack101
{
public static String encrpyt(String message, int key)
{
String cipherText = "";
for (int i = 0; i < message.length(); i++)
{
cipherText += (char)(((message.charAt(i) - 'A' + key) % 26) + 'A');
}
return cipherText;
}
public static String decrypt(String cipherText, int key)
{
String message = "";
for (int i = 0; i < cipherText.length(); i++)
{
message += (char)(((cipherText.charAt(i) - 'A' - key + 26) % 26) + 'A');
}
return message;
}
//A sample subset of most common 5 letters words
private static String[] knownWordsList = new String[] { "APPLE", "BEACH", "CLOCK", "HELLO", "JUICE", "MONEY", "SNACK", "WORLD"};
private static boolean checkIfKnownWord(char[] message) {
for (int i = 0; i < knownWordsList.length; i++)
{
if(knownWordsList[i].equals(new String(message)))
{
return true;
}
}
return false;
}
public static String hack(String cipherText)
{
//Take same cipher text as message
char[] message = cipherText.toCharArray();
for(char key = 1; key < 26; key++) {
for(int index = 0; index < cipherText.length(); index++) {
message[index] = (char)(((cipherText.charAt(index) - 'A' - key + 26) % 26) + 'A');
}
if(checkIfKnownWord(message))
return new String(message);
}
return null;
}
public static void main(String args[])
{
//Regular Crpytography
String message = "HELLO";
int key = 5;
String cipherText = encrpyt(message, key);
System.out.println("Original message : " + message);
System.out.println("Cipher message : " + cipherText);
System.out.println("Decrypted message : " + decrpyt(cipherText, key));
//Hacking
System.out.println("Hacked message without key : " + hack(cipherText));
}
}
Output
Original message : HELLO
Cipher message : MJQQT
Decrypted message : HELLO
Hacked message without key : HELLO
In 1975, DES: The natural bureau of standards invented Data Encryption Standard (DES) using 56-bit encryption. After 20 years the freedom foundation broke the DES key in 56 hours.
In 1977, RSA was invented by Ron Rivest, Adi shamir and Leonard Adleman at the Massachusetts institute of technology and it is based on the idea of a symmetric public-private key cryptosystem.
In 2001, AES: The Advanced Encryption Standard (AES) is a class of block cipher developed by two belgian cryptographers, vincent Rijmen and Joan Daemen. It can use key lengths of 128, 192 or 256 bits and it was announced by the Federal Information Processing Standard (FIPS) in 2001.
In 2005, ECC: The Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC requires small keys compared to non-EC cryptography to provide equivalent security.
Such modern algorithms are computationally secure, with no other theoretical weaknesses to make the algorithms less secure for practical purposes and of course brute force algorithms are not practically feasible. Even if a cryptography algorithm is computationally or mathematically secure, its implementation might be vulnerable to physical attacks. For example, The adventure of side channel analysis attacks are an efficient way to obtain the secret key.
In 1998, Paul Kocher et al. explained how to find secret keys by analyzing power consumption on the Data Encryption Standard (DES) . Power analysis, including Simple Power Analysis (SPA) and Differential Power Analysis (DPA), measures cryptographic device’s power consumption to disclose secret key material.
It starts by collecting power traces during cryptographic operation. After that, if the relevant information can be obtained directly from the trace pattern, then SPA will be applied. If it is not applicable, those traces will be statistically analyzed in order to derive the secret key of the cipher. This is called Differential Power Analysis.
Due to their observation, the attack has a success rate of 84% using a simple microphone and a PC. With Side-Channel attacks. People can break passwords without breaking the underlying algorithms.
A cipher is a secret code, usually an algorithm or a mathematical algorithm to convert the simple looking word or a message to encrypted text. As early codes substituted numerals for letters to hide the word’s meaning , codes are called ciphers.
Types of ciphers with Example
Substitution Cipher
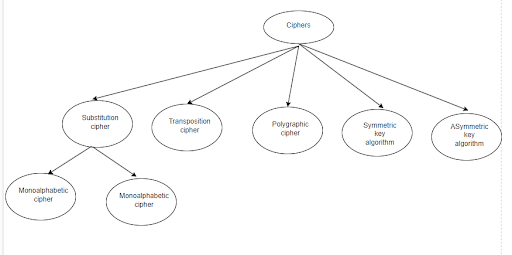
This cipher name itself says each letter is substituted by another letter. It is divided into two types :
- Monoalphabetic Cipher
- Polyalphabetic Cipher
Monoalphabetic Cipher
This is the first technique of substitution cipher. In the Caesar cipher algorithm, there are 26 possible cases to encrypt your plain text. So it is very easy to break using brute force technique. In Monoalphabetic algorithm, 26! Possible cases. So by using brute force technique, it is difficult and takes more time consuming when compared to caesar cipher algorithm. To encrypt the message , you need to substitute another letter for all the letters.
A | B | C | D | E | F | G | H | I | …….. | Z |
C | E | H | A | M | Q | F | P |
You have to remember one thing: no letter should be repeated . suppose you are substituting C for A then you cannot substitute for E also. This way I have to make one table. Now encryption is very simple.
Sender will send the encrypted message so that both receiver and sender knows the password (Key) to read the message.
Code
public class CaesarCipher
{
public static String encrpyt(String message, int key)
{
String cipherText = "";
for (int i = 0; i < message.length(); i++)
{
cipherText += (char)(((message.charAt(i) - 'A' + key) % 26) + 'A');
}
return cipherText;
}
public static String decrpyt(String cipherText, int key)
{
String message = "";
for (int i = 0; i < cipherText.length(); i++)
{
message += (char)(((cipherText.charAt(i) - 'A' - key + 26) % 26) + 'A');
}
return message;
}
public static void main(String args[])
{
String message = "HELLO";
int key = 5;
String cipherText = encrpyt(message, key);
System.out.println("Original message : " + message);
System.out.println("Cipher message : " + cipherText);
System.out.println("Decrypted message : " + decrpyt(cipherText, key));
}
}
Output
Original message : HELLO
Cipher message : MJQQT
Decrypted message : HELLO
Polyalphabetic Cipher
This is one of the other techniques of substitution cipher. This is the best known and simplest technique with another name called Vigenere Cipher. In this we use a matrix called the Vigenere matrix or Vigenere table. In this table, the vertical side is key and the horizontal side is plain text. The most important thing in this algorithm is to construct the cipher text; the length of the key should be equal to the length of the plain text or message. If it is not equal, I need to repeat the keyword as long as it matches with the size of the message..
For example:
Key : cipher
Message: Polyalphabetic
Key | c | i | p | h | e | r | c | i | p | h | e | r | c | i |
Message | p | o | l | y | a | l | p | h | a | b | e | t | i | c |
Let’s do coding that how a vigenere cipher works,
Code
public class VigenereCipher
{
public static String encrpyt(String message, String key)
{
String cipherText = "";
for (int i = 0; i < message.length(); i++)
{
cipherText += (char)(((message.charAt(i) + key.charAt(i)) % 26) + 'A');
}
return cipherText;
}
public static String decrpyt(String cipherText, String key)
{
String message = "";
for (int i = 0; i < cipherText.length(); i++)
{
message += (char)(((cipherText.charAt(i) - key.charAt(i) + 26) % 26) + 'A');
}
return message;
}
public static void main(String args[])
{
String message = "HELLO";
String key = "YATCH";
String cipherText = encrpyt(message, key);
System.out.println("Original message : " + message);
System.out.println("Cipher message : " + cipherText);
System.out.println("Decrypted message : " + decrpyt(cipherText, key));
}
Output
Original message : HELLO
Cipher message : FEENV
Decrypted message : HELLO
Let’s discuss the differences between the MonoAlphabetic cipher and Polyalphabetic cipher.
SI No | MonoAlphabetic cipher | PolyAlphabetic cipher |
1 | It is less secure when compared to Poly-alphabetic cipher. | It is less secure when compared to a mono-alphabetic cipher. |
2 | One single fixed alphabet is used for substitution. | More than one alphabet is used for substitution. |
3. | In this method, the same substitution rule is used for each substitution. | In this method, the substitution rule changes continuously from letter to letter according to the elements of the encryption key. |
4. | In this method, for a particular alphabet , only one substitution can be used. | In this method, any one alphabet substitutes with different alphabets using a vigenere table. |
5 | It can break easily. | It cannot break easily. |
6 | It included a caesar cipher. | It included a hill cipher. |
Transposition cipher
In the transposition cipher, the location of the letter is changed but its specification is not changed. Rearrange the order of plain text bits to provide security. In that substitution cipher, we are just replacing the character with a cipher text character. So in this cipher, we are not replacing the character but rearranging bit positions. In this technique, there are two main techniques, one is a rail fence cipher and another is row transposition cipher.
Let’s start with rail fence technique,
Ex: rail fence technique
r i f n e e h i u Plaintext
a l e c t c n q e
Cipher text : r i f n e e h i u a i e c t c n q e
This technique is used for only short lengths of messages. It can easily break down. I can easily be attacked by a third party.
Row transposition cipher
It is a more complex technique when compared to rail fence cipher but still it is a transposition technique Where the letter or alphabets are not substituted by other letters rather the position of the plain text is going to be changed.
First, consider the plain text and key. For the key, a unique number should be considered from 0 to 9.
Plain text = R o w t r a n s p o s i t i o n c i p h e r
Key = 3 2 4 5 1
3 2 4 5 1
R o w t r
a n s p o
s i t i o
n c i p h
e r x y z dummy characters.
Cipher text = r a s n e o n i c r w s t i x t p i p y r o o h z
Polygraphic ciphers
Polyfair is an example of polygraphic substitution cipher. Polygraphic is a substitution that involves replacing a group of characters in a message. It is a manual symmetric encryption technique. It means for both encryption and decryption same key is used. When the sender creating the cipher text then receiver also using the same key to decrypt the text. This is the first literal diagram substitution cipher. Basically it is a multiple letter encryption technique. This is not single letter encryption technique.
Symmetric key cryptography
In symmetric key cryptography, the main thing is that only one key is used by both the sender side and the receiver side. The same key is used for encryption as well as for the decryption process. The sender generates the message and encrypts it using a secret key, the receiver wants to decrypt it by applying the same secret key to convert plain text. The advantage is it can easily be implemented because of a single key. The disadvantage is using a single key it can be easily hacked.
Asymmetric key cryptography
In Asymmetric key cryptography, Two different keys are used. Those keys are public and private keys. The public key is known to everyone and the private key is only known to that person. The public key is used to encrypt a message and the private key is used for decrypting the message. The sender will generate the message using the receiver’s public key to encrypt and this encrypted message is sent to the receiver. Using the private key to decrypt the encrypted message. This is not that much more secure but secure when compared to symmetric key cryptography.
Let us discuss the differences between symmetric and asymmetric key cryptography.
Symmetric key | ASymmetric key |
It is also called private key cryptography or secret key cryptography. It uses only one key for both encryption and for decryption. | It is also called public key cryptography. It uses 2 different keys (Public and private key) for encryption and for decryption. |
Performance: Faster in execution. | Slower in execution. |
It is less complex and less computational power is required. | It is more complex and more computational power is required. |
It is used for the transfer of bulk data. | It is used for secretly exchanging the secret key. |
Sharing the key between the sender and receiver is not safe. Commonly used symmetric algorithms: DES, AES, 2DES, 3DES, RC4 | The problem of symmetric keys is solved here because of the private key concept. Commonly used Asymmetric algorithms: RSA, Deffie hellman key exchange, DSA. |